In this article, we’ll review the types of malicious software and recommended measures to keep your business safe.
Years ago, computer viruses and malware were on the top of everyone’s mind. Back when Windows XP was the most common operating system, viruses and especially malware seemed to constantly infect computers. Over the past decade, however, the number and reliability of security measures have increased, especially within operating systems such as Windows 7 and Windows 10. However, this doesn’t mean the threat has disappeared; in fact, ransomware has recently been in the news again, with reports of hundreds of thousands of infected computers.
Malware
Of the three types of malicious software—malware, viruses, and ransomware—malware is the least dangerous. Malware usually consists of software that looks like a legitimate program or tool. Sometimes, it exhibits a useful functionality, but in the background, it records and captures all your personal information and slows down your computer. Common annoyances include pop-up ads while browsing the Internet, toolbar pop-ups aiming to convince you to buy something, and intrusions that take over your Web browser’s toolbars or change your search page. A common malware program, for example, is the “Ask Toolbar,” which I am sure we have all accidently installed. Malware usually will not lead to a broken computer or a loss of information, but it can lead to a loss of privacy and a degradation of the performance and functionality of your computer.
Malware is usually installed by “piggybacking” on other, more legitimate software. For example, if you download a free music player onto your computer, when you complete the installation process, be careful to check for any “bonus” or additional software that the download utility is trying to install. The screenshot below illustrates what this typically looks like.
You can see that this software is trying to install the Yahoo! search bar and other miscellaneous software; the additional components, posing as applications that will provide useful functionality, constitute malware that will slow down your machine and take over certain features. To bypass this malware and prevent installation of the supplemental software, the user must choose “Decline.” However, most people do not pay attention to the process and instead blindly choose “Next” or “Accept” to finish the installation. Keeping a close eye on your software installation will help keep your computer malware-free.
Another way that malware makes its way onto your computer is through Internet browser pop-ups. If you see this type of pop-up, be wary:
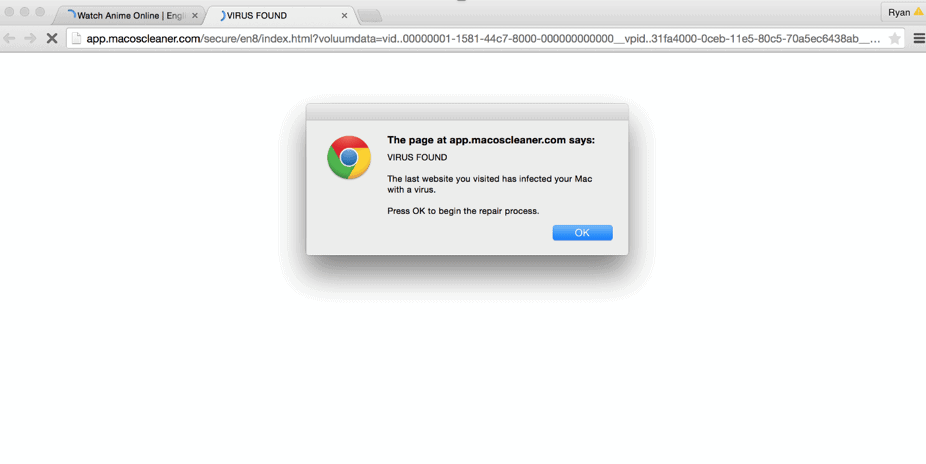
If you do happen to install malware onto your computer, you at least have a recourse: you can remove it with an anti-malware program. The best one currently on the market is Malwarebytes (https://www.malwarebytes.com) and is free to use.
Viruses
Viruses are very different from malware and much more harmful. Where malware tries to stay within the legal realm and only record data from your machine or slow it down, a virus aims to completely take over your machine, destroy it, or find confidential but valuable information such as credit card numbers. Viruses also do not “hide in plain sight” like malware installations. Viruses will usually install in the background with no notification, and you will not know you are infected until your computer starts having performance issues. A virus may even sit silently in the background for weeks or months at a time without the user knowing it exists; such a virus is sometimes called a time bomb.
Viruses are usually installed from an e-mail attachment or a storage medium, such as a USB flash drive. The most important things to look for are suspicious attachments to your e-mails or even suspicious e-mails altogether. Whenever you see an email that does not look legitimate, it is better to simply delete it rather than risk opening it or downloading any attachments. Be especially wary of any .exe files from sources that you do not trust. These are executable files, and when the files are run they could be used to install a virus. Viruses can also be embedded within common document file types (e.g., .doc, .xls, .pdf) or within .bat files or many other file types.

Getting rid of viruses is not always easy. The best way is to use an anti-virus program from trusted companies, such as Norton or McAfee. There are also a few newer anti-virus products on the market, such as Bitdefender and Avast. If a software program will not remove your virus, a backup or system restoration for your computer may restore the machine to a pre-virus state.
Ransomware
Ransomware is a type of virus. However, because it has become so common and is by far the most dangerous of the viruses, it is worth talking about as its own topic. Among the dangers is that ransomware cannot be removed with an anti-virus program and many times it cannot be removed with a restore point or system restore either. A backup of your files is the only defense!
Ransomware gets onto your machine just like any other virus, most commonly through e-mail attachments. Once it has been loaded on your machine, it runs itself in the background, and the user will have no idea that the machine has been infected. Over the next few hours or days, when the machine is on, the ransomware will run in the background and encrypt every file on the computer. Encryption is a type of encoded security, rendering a file unreadable except by the person who has a key to unlock the file. And guess who has that key? The hackers who created the ransomware.
What this means is that all your documents, photos, music files, video files, and everything else of value will not be accessible without the key. The hackers who made the virus will gladly give you that key—for a fee! That is why it is called “ransomware.” The fee for the key is not cheap—usually a few hundred dollars. And there is usually a time limit to pay the ransom. In addition, payment introduces a new liability because during the transaction the hackers may steal your credit card information or initiate other similarly terrible things. However, many victims pay the ransom because they need valuable information from their computer that cannot be replaced; thus, the use of ransomware has continued to grow. Losses are estimated at tens of millions of dollars at this point. The hackers have a huge incentive to keep developing these viruses!
Again, no anti-virus application can decrypt the files on your computer. Usually, the ransomware will also corrupt any restore points (system restores). The ransomware may even encrypt files stored on attached media devices, so external hard drives and USB drives will also be infected. The only defenses are a backup of your computer saved to an external drive that you disconnect after the backup is made and a similar computer backup stored in the cloud. Security experts recommend that you back up your machine at least once a month and keep the backup on a separate drive or use a cloud-based storage service.
Here is what ransomware may look like after an infection:
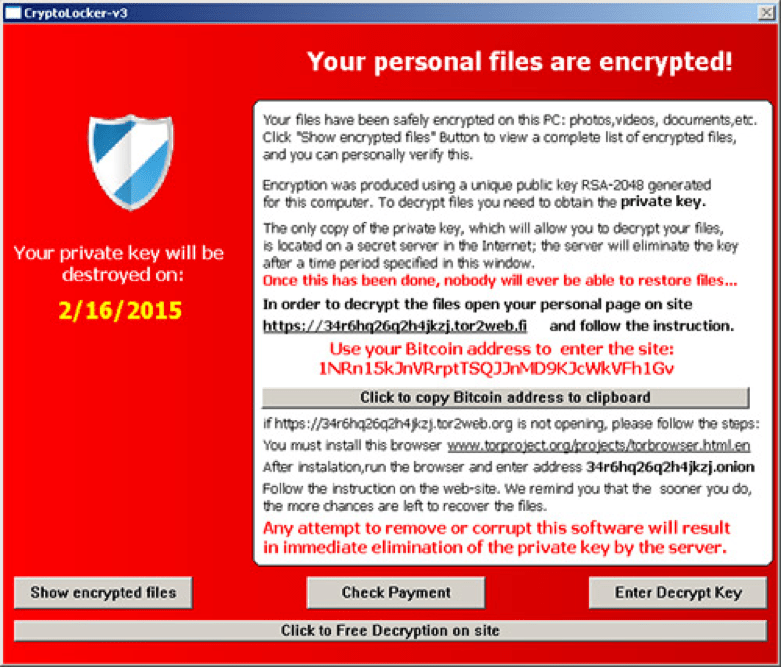
The Bottom Line
Malware, viruses, and ransomware are still common and, indeed, even proliferating and growing more sophisticated in today’s world. Computer users should exercise constant diligence to maintain the safety of their computers and their information. Fortunately, just a few rules and best practices need to be followed: Install software or accept pop-ups from trusted companies and websites. Open e-mail attachments from sources you know and trust. Scrutinize e-mail addresses and website URLs to make sure they are legitimate. And keep a regular backup of your machine handy in case anything should happen.
About Ocreative
Ocreative was established in 2003 as one of the early pioneers of digital advertising and design in the Midwest. The company is made up of bright, honest digital innovators and creative gurus, carving out a niche for themselves and their trusting clients. Along the way, Ocreative has grown to become more recognized as an award-winning, full-service, integrated marketing agency. Ocreative gets big results for its clients, and that puts big smiles on everyone’s faces. Even though the agency’s office is in the Midwest, its clients are located throughout the United States. Ocreative’s portfolio includes expert marketing and strategy, advertising and design, websites and digital marketing, video, and multimedia.





